Data Science In Cyber Security has become an indispensable tool in many industries, including Cybersecurity. With the increasing complexity and sophistication of cyber attacks, it has become crucial for organisations to implement robust cybersecurity measures.
Data Science provides organisations with the ability to detect and prevent cyber attacks, thus improving their Cybersecurity posture.
This blog will explore the importance of Data Science in Cybersecurity and its various applications.
What Is Cybersecurity?
Cybersecurity refers to the practice of protecting computer systems, networks, and digital assets from unauthorised access, theft, or damage. The increasing reliance on digital technologies in all aspects of our lives has made cybersecurity more important than ever before. Threats to cybersecurity can take many different forms, including:
- Malware: Malware refers to malicious software that is designed to damage or disrupt computer systems or steal sensitive data. Malware commonly comes in the form of viruses, worms, Trojan horses, and ransomware.
- Phishing: Phishing is a type of social engineering attack in which attackers try to trick users into divulging sensitive information, such as passwords or credit card numbers, by posing as a trustworthy entity in an email or message.
- Denial Of Service (DOS) Attacks: A system or network is targeted during a DoS attack in an effort to overwhelm it with traffic and render it inaccessible to users. Distributed Denial of Service (DDoS) attacks use multiple systems to launch an attack, making them even more difficult to stop.
- Man-In-The-Middle (MITM) Attacks: MitM attacks involve intercepting communication between two parties to steal data or inject malicious code.
Why Is Cybersecurity Important?
Cybersecurity is important because it helps protect sensitive data, prevents financial losses, and maintains public safety. A successful cyber attack can result in devastating consequences, including:

- Theft of intellectual property or personal data
- Loss of revenue due to system downtime or data breaches
- Reputation damage and loss of customer trust
- Compromised national security or public safety
Applications Of Data Science In Cybersecurity
The use of Data Science in Cybersecurity has become crucial in today's technology-driven world. Let's explore its various applications in detail.
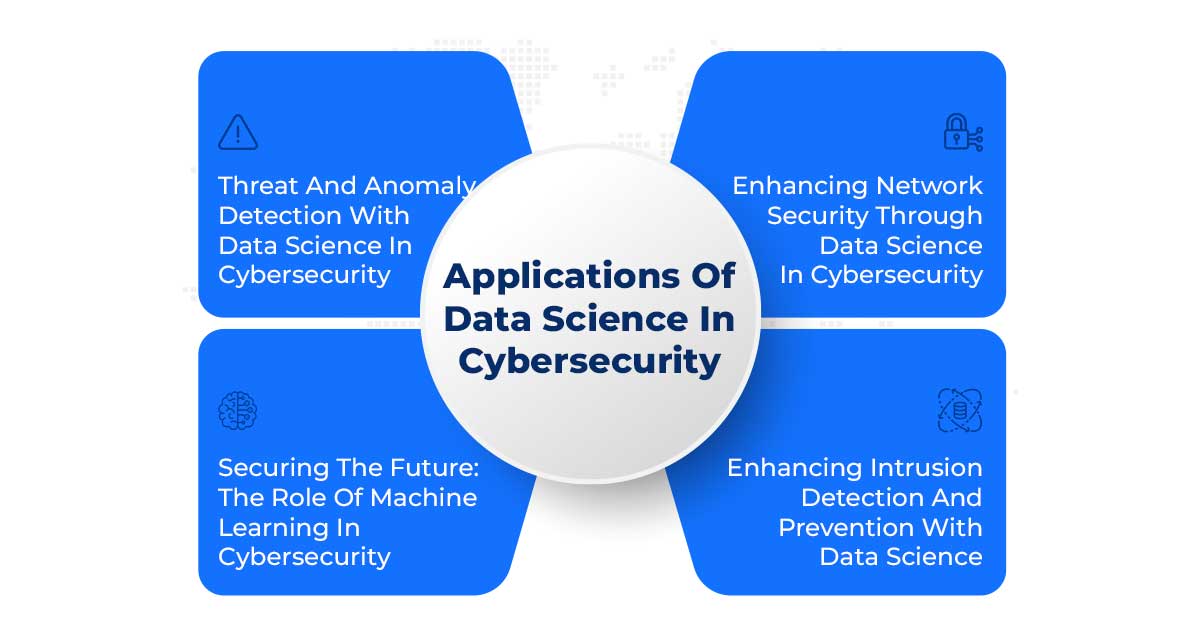
1. Threat And Anomaly Detection With Data Science In Cybersecurity
Threat Detection and Anomaly Detection are crucial components of Cybersecurity. Threat Detection involves identifying potential security threats, while Anomaly Detection involves identifying abnormal behavior or events that may indicate a security breach. Data Science can be used to improve Threat Detection and Anomaly Detection in the following ways:
- Machine Learning algorithms can be used to analyze vast amounts of data and identify potential security threats and abnormal behavior
- Predictive analytics can be used to predict potential security threats and anomalous behavior, allowing organizations to take preventive measures.
- Statistical analysis can be used to identify unusual activities and behaviors that may indicate a security breach.
- Behavioral analysis can be used to identify patterns in user behavior and network traffic that may indicate a security breach.
- Pattern recognition can be used to identify known security threats and prevent them from occurring.
By leveraging Data Science techniques in Threat Detection and Anomaly Detection, organizations can improve their Cybersecurity posture and better protect themselves against cyber attacks.
2. Enhancing Network Security Through Data Science In Cybersecurity
Network Security is a crucial aspect of Cybersecurity. Data Science plays a critical role in Network Security by providing organizations with tools to detect and prevent security breaches. Below are some ways in which Data Science is used in Network Security:
- Anomaly Detection: Data Science algorithms can be used to detect unusual patterns or behaviors in network traffic, which may indicate a security breach.
- Real-Time Monitoring: Data Science tools can be used to monitor network traffic in real time, allowing organizations to detect and respond to security breaches quickly.
- Predictive Analytics: Predictive analytics can be used to identify potential security breaches and take preventive measures to avoid them.
Moreover, Network Security in Data Science for Cybersecurity involves the following aspects:
- Threat Intelligence: Data Science can be used to analyze threat intelligence data from various sources and identify potential security threats.
- Network Segmentation: Data Science can be used to analyze network traffic and segment networks based on different security levels, reducing the attack surface for potential cyber attacks.
- Identity And Access Management: Data Science can be used to analyze user behavior data and identify potential security breaches related to identity and access management.
3. Securing The Future: The Role Of Machine Learning In Cybersecurity
Machine Learning (ML) is a subset of Artificial Intelligence (AI) that enables systems to learn and improve from experience without being explicitly programmed. ML has several applications in Cybersecurity, including Threat Detection, Anomaly Detection, and Network Security. Below are some of the ways in which Machine Learning is used in Cybersecurity:
- Threat Detection: ML can be used to detect and classify different types of cyber threats, such as malware, phishing, and ransomware.
By analyzing large datasets of historical threat data, ML algorithms can identify patterns and characteristics that indicate the presence of a particular type of threat.
- Anomaly Detection: ML can be used to detect anomalies in network traffic, user behavior, and other data sources that may indicate a security breach.
ML algorithms can learn the normal patterns of behavior and identify deviations from these patterns that may indicate a security breach.
- Network Security: ML can be used to improve network security by identifying potential vulnerabilities and predicting the likelihood of a security breach.
By analyzing network traffic and other data sources, ML algorithms can identify patterns and characteristics that indicate a potential attack and take preventive measures to protect the network.
- Intrusion Detection: ML can be used to detect and prevent intrusions by analyzing network traffic and other data sources to identify potential security breaches.
By learning the normal patterns of activity and identifying deviations from these patterns, ML algorithms can detect and prevent unauthorized access to sensitive data and systems.
4. Enhancing Intrusion Detection And Prevention With Data Science
Intrusion Detection and Prevention are essential components of Cybersecurity. Intrusion Detection involves identifying potential security breaches, while Intrusion Prevention involves preventing security breaches from occurring. Data Science can be used in the following ways to improve Intrusion Detection and Prevention:
- Behavioural Analysis: Data Science can be used to analyze user behaviour and identify anomalies that may indicate a security breach. By identifying patterns and anomalies in user behaviour, Data Science can help detect and prevent unauthorized access to sensitive data and systems.
- Network Analysis: Data Science can be used to analyze network traffic and identify potential security threats. By monitoring network traffic and identifying unusual patterns, Data Science can help detect and prevent network-based attacks.
- Threat Intelligence: Data Science can be used to analyse threat intelligence data and identify potential security threats. By monitoring threat intelligence feeds and analyzing data from various sources, Data Science can help organizations stay ahead of emerging threats and take proactive measures to prevent security breaches.
- Real-Time Monitoring: Data Science can be used to monitor network activity in real-time and detect potential security breaches as they occur. It helps organizations respond to security breaches quickly and prevent them from causing significant damage.
Challenges Of Implementing Data Science In Cybersecurity
Implementing Data Science in Cybersecurity poses several challenges and limitations, some of which are listed below:

- Data Quality: Data Science requires high-quality data, which can be a challenge in Cybersecurity, where data is often incomplete, inconsistent, or inaccurate.
- Skilled Personnel: Implementing Data Science in Cybersecurity requires skilled personnel, which can be a challenge due to the shortage of skilled personnel in this field.
- Cost: Implementing Data Science in Cybersecurity can be costly, as it requires specialized tools
- Lack Of Standards: There is currently a lack of standardization in the field of Cybersecurity, making it difficult to develop a unified approach to implementing Data Science in Cybersecurity.
- Privacy Concerns: With the increasing use of data in Cybersecurity, there is a growing concern about privacy. Implementing Data Science in Cybersecurity can raise privacy concerns as it involves analyzing sensitive data.
- Adversarial Attacks: Adversarial attacks are a type of cyber attack that aims to deceive machine learning models. Implementing Data Science in Cybersecurity can make organizations more vulnerable to these types of attacks.
Real-World Examples Of Data Science In Action For Cybersecurity
These examples demonstrate the power of Data Science in Cybersecurity and how it is being used by leading Cybersecurity companies to protect against cyber threats.
- Darktrace: An artificial intelligence (AI)-powered cybersecurity platform that uses machine learning algorithms to quickly identify and address online threats.
- Splunk: A data analytics platform that provides security information and event management (SIEM) capabilities, enabling organizations to identify potential security threats and take action to mitigate them.
- FireEye: A Cybersecurity company that uses machine learning and other advanced technologies to detect and respond to cyber threats. FireEye's Threat Intelligence platform provides real-time threat analysis and incident response capabilities.
- IBM Security: IBM Security provides a range of Cybersecurity solutions, including threat detection and response, risk management, and compliance monitoring. IBM detects possible security threats and reacts to them instantly using powerful analytics and machine learning techniques.
- Symantec: Symantec is a leading provider of Cybersecurity solutions, including antivirus software, intrusion detection and prevention, and data loss prevention. Symantec uses machine learning and other advanced technologies to identify and respond to cyber threats.
-
Future Of Data Science In Cybersecurity: Advancements And Trends

As the world becomes more digitized, the number of cyber attacks continues to increase, making it essential for organizations to implement advanced security measures. Here are some additional pointers on the future of Data Science in Cybersecurity:
- Big Data Analytics: With the increasing amount of data generated by organizations, Big Data Analytics will become an essential component of Cybersecurity. It will help in analyzing data to detect and respond to security threats.
- Predictive Analytics: Predictive Analytics is a technique used in Data Science to predict future events based on historical data. It can be used in Cybersecurity to detect and prevent cyber attacks before they occur.
- Cloud Security: As organizations move their data to the cloud, there is a growing need for cloud security. Data Science can be used to develop cloud security solutions that can detect and respond to security threats in real time.
- Cyber Threat Intelligence: Cyber Threat Intelligence is the analysis of information about potential cyber threats. Data Science can be used to develop Cyber Threat Intelligence solutions that can provide organizations with valuable insights into potential security threats.
- Privacy Protection: With the increasing use of data in Cybersecurity, there is a growing need for privacy protection. Data Science can be used to develop privacy protection solutions that can protect personal data from cyber threats.
A Word From Ekeeda
Data Science has revolutionized the Cybersecurity industry, providing organisations with the ability to detect and prevent cyber-attacks.
As the Cybersecurity landscape continues to evolve, the role of Data Science will become increasingly important, and Ekeeda can help individuals stay up-to-date with the latest advancements in this field.
Frequently Asked Questions
What Role Does Data Science Play in Cybersecurity?
Data Science provides organizations with the ability to detect and prevent cyber attacks, thus improving their Cybersecurity posture.
What Are The Applications Of Data Science In Cybersecurity?
Data Science has numerous applications in Cybersecurity, including Cyber Attack prediction and prevention, identifying patterns and trends, and enhancing an organization's Cybersecurity posture.
What Are The Challenges Of Implementing Data Science In Cybersecurity?
Challenges to implementing Data Science In Cyber Security include data quality, skilled personnel shortage, and cost.
How Can Machine Learning Be Used In Cybersecurity?
Machine Learning algorithms can analyze vast amounts of data, predict potential security breaches, and identify patterns and anomalies.
How Can Ekeeda Help Individuals Interested In Learning About Data Science In Cybersecurity?
Ekeeda offers online courses on Data Science that cover topics such as Machine Learning, Statistical analysis, and Anomaly Detection, providing individuals with the necessary skills to implement Data Science in Cybersecurity.